
multicast authentication based on batch signature

Server SSL authentication - certificate creation and distribution

Multicast address format.
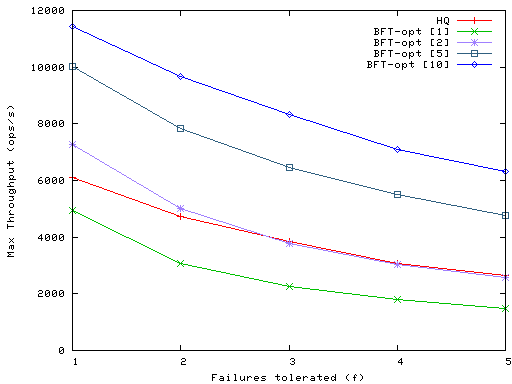
Figure 9: Effect of BFT batching on maximum write throughput.

multicast authentication based on batch signature

multicast authentication based on batch signature
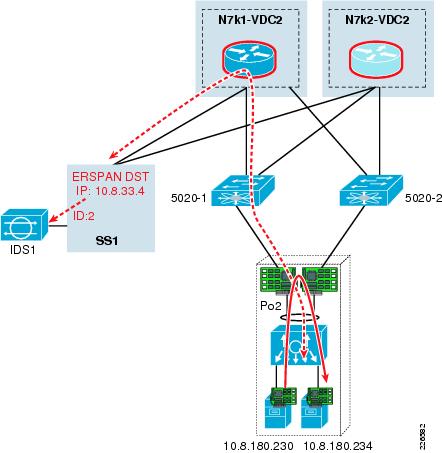
The attempt triggers a signature on the IDS and is logged for investigation.

Figure 13: Batch rekeying vs. individual rekeying.

The following processes need to be carried out to implement authentication

The authentication process involves verification of user credentials,

Authentication server uses a relational database model to store students'

Triangular based pyramid. Triangular prism. Hexagonal prism

Triangular-based pyramid, Ovoid, Rectangular prism and Triangular prism.

Based on the base, the prisms are defined as triangular prism, square prism,

Pictures authorization Pictures auth structural digital signature for image authentication Photo phindings: image authentication photobucket | jsa

Authentication server uses a relational database model to store students'

Ensure 'Multicast' option is selected along with 'IGMP Multicast'.

Chief Crazy Horse Mountain in Montana, and the Indians were led by Chief

"Tuesdays With Morrie". by Jeffrey Hatcher and Mitch Albom, based on the
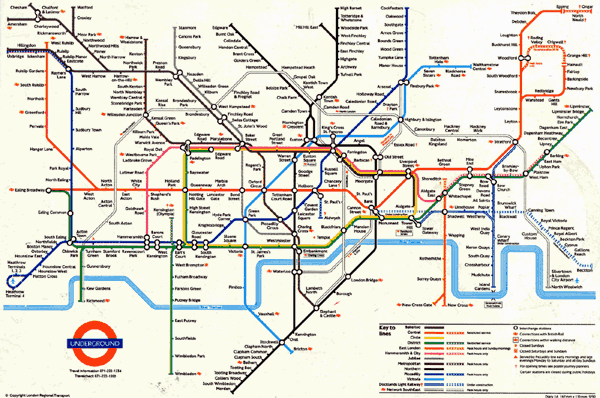
Figure 1: London Underground diagram of 1991, still based on the original
No comments:
Post a Comment